The exponential proliferation of unmanned aircraft systems across commercial, governmental, and civilian applications has fundamentally transformed both the opportunities and threat landscapes in modern airspace, creating unprecedented security challenges where traditional cybersecurity frameworks must integrate seamlessly with kinetic defense systems and electromagnetic warfare considerations. Modern drone ecosystems represent complex multi-domain attack surfaces encompassing airborne platforms, ground control infrastructure, communication networks, cloud-based fleet management systems, and mobile applications that collectively create vulnerability matrices requiring sophisticated security architectures to address effectively. The complexity of securing these distributed systems mirrors challenges found in other high-stakes technological environments where comprehensive security protocols must protect valuable assets and sensitive operations across multiple interconnected platforms, much like how robust documentation and transparency frameworks establish trust and security in complex technological systems through clear operational procedures and accountability mechanisms.
The economic implications of drone security failures extend far beyond immediate operational disruption to encompass long-term reputational damage, regulatory penalties, competitive intelligence theft, and potential liability for damages caused by compromised systems. Corporate drone operations increasingly handle sensitive data including proprietary facility layouts, infrastructure vulnerabilities, agricultural intelligence, and environmental monitoring information that represents significant competitive value to adversaries. The hidden costs of inadequate security include business disruption from successful attacks, regulatory compliance failures, insurance premium increases, and opportunity costs from restricted operations in security-sensitive environments, creating total cost structures that often exceed visible operational expenses. Understanding comprehensive cost implications becomes essential for justifying security investments and developing appropriate risk management strategies, similar to how transparent fee structures and operational costs enable informed decision-making in complex technological environments where hidden expenses can significantly impact total operational economics.
The convergence of cyber and physical threat vectors in drone security creates unique challenges where information security approaches must integrate with kinetic defense systems, electromagnetic warfare considerations, and physical access controls to create comprehensive protection frameworks. Modern threat actors possess capabilities ranging from sophisticated nation-state cyber operations to readily available consumer-grade counter-drone technologies, creating threat landscapes where organizations must simultaneously defend against advanced persistent threats and opportunistic attacks using commodity hardware. This multi-domain threat environment requires security strategies that address technical vulnerabilities, operational procedures, regulatory compliance, and incident response capabilities across diverse attack scenarios and threat actor motivations.
Comprehensive Threat Landscape Analysis
Understanding the contemporary drone threat environment requires systematic analysis of adversary categories, their capabilities, motivations, and preferred attack methodologies. This threat landscape encompasses state-sponsored actors possessing advanced capabilities including custom malware development, zero-day exploit deployment, signals intelligence collection, and coordinated multi-vector attacks that can compromise entire drone ecosystems through systematic exploitation of multiple vulnerability classes simultaneously. These adversaries typically target high-value intelligence including critical infrastructure layouts, military installations, industrial processes, and government operations, employing long-term persistence strategies that can remain undetected for extended periods while continuously exfiltrating sensitive information.
Criminal organizations increasingly target drone operations for financial gain through ransomware deployment, data theft for underground market sales, industrial espionage services, and direct extortion of organizations dependent on drone operations for critical business functions. These threat actors typically employ readily available tools and techniques adapted from broader cybercriminal ecosystems, focusing on high-probability attack vectors that provide rapid return on investment with minimal technical complexity. Criminal drone attacks often target fleet management systems, cloud storage repositories, and payment processing systems associated with commercial drone services, seeking to maximize financial impact while minimizing exposure to law enforcement detection.
Terrorist organizations and extremist groups present unique threat profiles combining ideological motivation with increasingly sophisticated technical capabilities, often targeting symbolic infrastructure, public events, and government facilities using drones as delivery platforms for explosive devices, chemical agents, or surveillance equipment. These adversaries typically employ commercially available drones modified with custom payloads and control systems, leveraging open-source intelligence and readily available technical information to develop attack capabilities that can evade conventional security measures.
Competitive intelligence operations represent a growing threat category where corporate adversaries employ drone-based surveillance, data interception, and operational disruption to gain competitive advantages through industrial espionage, market intelligence collection, and strategic business disruption. These attacks often target proprietary processes, facility layouts, personnel movements, and operational timing to provide competitive intelligence that can be leveraged for strategic business advantages.
Advanced Cyber Attack Vectors and Technical Exploitation Methods
Modern drone systems present extensive cyber attack surfaces encompassing multiple interconnected components that collectively create complex vulnerability landscapes requiring comprehensive security analysis. GPS spoofing attacks represent one of the most accessible and impactful cyber attack vectors, exploiting the fundamental reliance of most unmanned aircraft systems on Global Navigation Satellite System signals for positioning, navigation, and timing functions. Sophisticated GPS spoofing equipment can generate false satellite signals that appear legitimate to target drone systems, enabling attackers to manipulate aircraft positioning data and potentially cause controlled crashes, unauthorized landing, or redirection to attacker-controlled locations.
Radio frequency jamming attacks target communication links between ground control stations and unmanned aircraft, potentially causing loss of command and control, forced autonomous landing procedures, or complete mission failure depending on aircraft autonomous capabilities and failsafe configurations. Modern jamming equipment can target specific frequency bands used by popular drone control protocols while avoiding interference with other radio services, enabling targeted attacks that minimize collateral impact and reduce detection probability.
Protocol exploitation attacks target vulnerabilities in communication protocols used between ground control stations and aircraft systems, potentially enabling unauthorized command injection, data interception, and man-in-the-middle attacks that compromise both aircraft control and data security. Many commercial drone systems employ proprietary communication protocols that lack robust authentication and encryption mechanisms, creating opportunities for attackers to inject malicious commands or intercept sensitive operational data including video streams, telemetry information, and mission parameters.
Firmware and software exploitation represents sophisticated attack vectors targeting vulnerabilities in drone operating systems, flight control software, and companion applications to achieve persistent compromise of target systems. These attacks typically require detailed reverse engineering of target systems and custom exploit development, but can provide comprehensive system access including flight control manipulation, data exfiltration, and persistent backdoor installation that survives normal system updates and maintenance procedures.
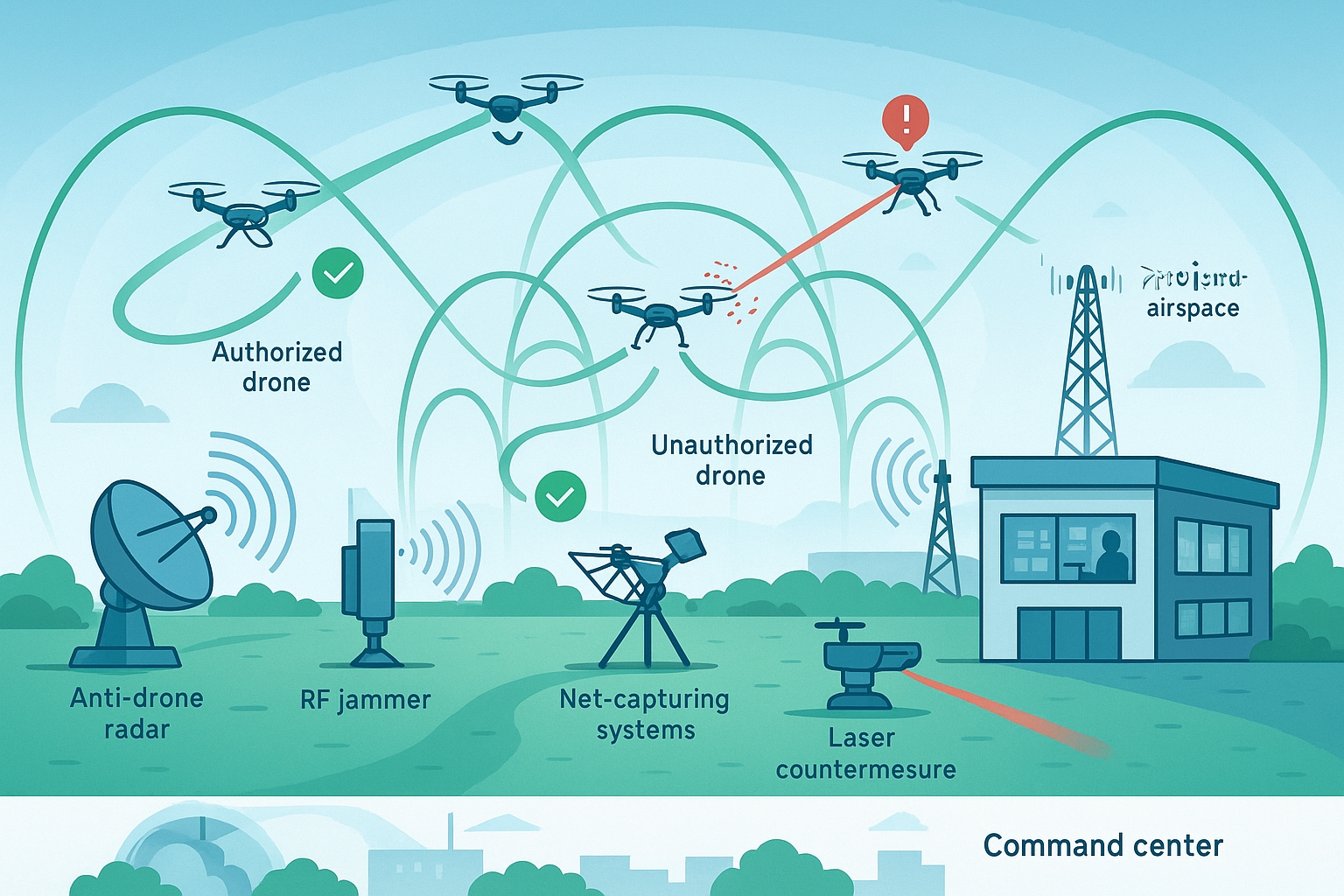
Physical Threat Vectors and Counter-UAS Technologies
Physical threats against drone operations encompass both direct attacks on aircraft and ground infrastructure, as well as sophisticated counter-drone technologies that can disable or capture target systems through various kinetic and non-kinetic methods. Kinetic interdiction methods represent the most direct approach to drone threat neutralization, employing projectile weapons, interceptor aircraft, or directed energy systems to physically disable or destroy target drones through direct impact or structural damage.
Professional counter-drone systems increasingly employ specialized interceptor drones equipped with nets, electromagnetic pulse generators, or collision mechanisms designed to disable target aircraft while minimizing collateral damage to surrounding infrastructure and personnel. Advanced kinetic systems may incorporate artificial intelligence and autonomous targeting capabilities that enable rapid engagement of multiple target drones simultaneously while maintaining discrimination between legitimate and threat aircraft.
Electromagnetic warfare techniques target drone electronic systems through high-power microwave emissions, electromagnetic pulse generation, or directed radio frequency attacks that can disable flight control systems, navigation equipment, and communication links without causing physical damage to aircraft structures. These non-kinetic attack methods can potentially disable multiple aircraft simultaneously across wide geographic areas, making them particularly effective against drone swarm attacks or coordinated multi-aircraft operations.
Capture and hijacking techniques attempt to gain control of target drones through exploitation of control protocols, signal injection, or physical capture using specialized equipment designed to override legitimate operator commands and redirect aircraft to attacker-controlled locations. These attacks typically require sophisticated technical capabilities and real-time signal analysis to identify and exploit specific vulnerabilities in target communication systems.
Multi-Layered Defense Architectures and Implementation Strategies
Effective drone security requires comprehensive defense-in-depth strategies that integrate cryptographic protection, anti-spoofing technologies, anomaly detection systems, and physical security measures to create robust protection against diverse threat vectors. Security architecture must begin with an immutable root of trust and measured boot processes, where airborne and ground systems verify every firmware stage using vendor keys pinned in hardware, record measurements for remote attestation, and refuse to operate mission functions if chain-of-trust checks fail.
Command-and-control link security requires defense-in-depth approaches combining frequency agility, link-layer encryption, and application cryptography with mutual authentication, sequence enforcement, and replay resistance mechanisms. Cellular and satellite communication backhauls reduce jamming susceptibility but introduce credential and roaming risks that must be mitigated through per-flight ephemeral identities with narrow scopes and broker systems that deny opaque paths from internet to flight computers.
Navigation integrity systems must assume that GNSS signals can be compromised and implement multi-constellation, multi-frequency receivers with tightly coupled inertial navigation systems, barometric altitude sensors, visual-inertial odometry, and magnetometer sanity checks. Spoofing-resistant receivers leverage correlation checks, signal quality metrics, and time-of-arrival anomalies, while autonomy logic responds to any divergence by degrading gracefully and constraining speed, altitude, and proximity to no-fly risks.
Payload and data protection requires encryption on ingress, processing in memory-guarded sandboxes, and storage with at-rest encryption keys rolled per sortie. Downlinks must avoid ad-hoc peer connections, routing every exchange through authenticated channels with data-loss prevention rules enforcing region, retention, and redaction policies. Model and firmware updates reaching the payload compute should pass through the same signature checks as flight software.
Advanced Detection and Monitoring Technologies
Comprehensive drone security requires sophisticated detection and monitoring capabilities that can identify potential threats across multiple sensor modalities while maintaining low false alarm rates and providing actionable intelligence for response teams. Radar-based detection systems provide primary surveillance capabilities through specialized configurations optimized for small, slow-moving targets, employing advanced signal processing techniques including Doppler filtering, micro-Doppler analysis, and machine learning algorithms to distinguish between legitimate aircraft, birds, and potential drone threats.
Radio frequency monitoring systems detect and analyze communication signals between drones and control stations, providing identification of drone types, operational parameters, and potential command and control vulnerabilities. Advanced RF monitoring systems perform real-time protocol analysis to identify specific drone models, decode telemetry information, and potentially intercept video streams or mission data that provide intelligence about threat actor intentions and capabilities.
Electro-optical and infrared detection systems provide visual confirmation of detected targets while enabling detailed analysis of aircraft configurations, payload characteristics, and operational behavior patterns. Advanced optical systems incorporate artificial intelligence algorithms trained on extensive drone imagery databases to provide automated target classification and threat assessment capabilities that reduce operator workload while improving detection accuracy.
Acoustic detection systems complement other sensor modalities by detecting characteristic sound signatures produced by drone propulsion systems, enabling detection of aircraft that may evade radar or optical detection through stealth design or operational techniques. Machine learning algorithms trained on extensive acoustic signature databases can identify specific drone models and estimate operational parameters including altitude, speed, and proximity based on acoustic characteristics.
| Detection Technology | Primary Capabilities | Detection Range | Key Advantages | Limitations |
| Multi-Static Radar | Small target detection, velocity measurement, track correlation | 5-15 km typical | All-weather operation, precise tracking, difficult to jam | High cost, requires clear line-of-sight, bird interference |
| RF Monitoring | Protocol analysis, drone identification, C2 interception | 1-10 km depending on power | Passive operation, detailed intelligence, low false alarms | Requires known protocols, ineffective against autonomous drones |
| EO/IR Systems | Visual confirmation, payload analysis, behavioral assessment | 1-5 km typical | Positive identification, detailed analysis, evidence collection | Weather dependent, requires operator attention, limited range |
| Acoustic Arrays | Sound signature analysis, direction finding, stealth detection | 0.5-2 km typical | Covert operation, works in RF-denied environments | Limited range, environmental noise interference |
Incident Response and Recovery Frameworks
Comprehensive drone security requires well-developed incident response capabilities that can rapidly detect, contain, and recover from security incidents while preserving evidence for investigation and preventing similar future incidents. Incident detection systems must provide rapid identification of potential security incidents through automated monitoring of system logs, network traffic, aircraft telemetry, and operational parameters that may indicate compromise or attack.
Advanced detection systems employ machine learning algorithms trained on normal operational patterns to identify anomalous behavior that may indicate security incidents, while correlation engines analyze multiple data sources to identify complex attack patterns that may not be apparent through individual system monitoring. Incident classification frameworks should provide standardized severity ratings and response procedures that enable consistent and appropriate response to different types of security incidents.
Containment and mitigation procedures must rapidly limit the scope and impact of security incidents while preserving system functionality for critical operations and maintaining evidence integrity for subsequent investigation. Automated containment systems should isolate compromised systems, terminate suspicious network connections, and implement emergency operational procedures without requiring immediate human intervention.
Recovery and restoration procedures ensure normal operations can be resumed quickly following security incidents while implementing appropriate security improvements to prevent similar future incidents. Recovery procedures should address system restoration from secure backups, security validation of restored systems, and incremental return to normal operations while maintaining enhanced monitoring for signs of persistent compromise.
| Response Phase | Target Timeline | Primary Actions | Success Metrics | Escalation Triggers |
| Detection | <60 seconds from first indicator | Automated anomaly flagging, alert generation | Time to detection, false positive rate | Multiple simultaneous alerts, high-confidence threats |
| Assessment | <5 minutes for initial triage | Threat correlation, impact analysis, stakeholder notification | Classification accuracy, response team engagement time | Critical infrastructure impact, safety risks |
| Containment | <30 minutes for isolation | System quarantine, emergency procedures, evidence preservation | Containment effectiveness, operational continuity | Spreading compromise, control system impact |
| Recovery | <4 hours for basic restoration | System validation, incremental restoration, monitoring enhancement | Recovery time, system integrity verification | Persistent indicators, recurring incidents |
Regulatory Compliance and Legal Framework Integration
Drone security operations must navigate complex regulatory environments encompassing aviation safety requirements, cybersecurity standards, privacy protection laws, and sector-specific regulations that collectively create comprehensive compliance obligations. Aviation security regulations increasingly address drone operations through requirements for remote identification, operator certification, operational restrictions, and security screening procedures that must be integrated with broader cybersecurity and physical security measures.
Remote ID requirements mandate that drone operations provide real-time identification and location information that can be monitored by law enforcement and security agencies, creating new security considerations around data privacy, operational security, and potential surveillance by adversaries. Compliance with aviation security regulations requires coordination between security teams, flight operations personnel, and regulatory affairs specialists to ensure security measures support rather than conflict with aviation safety and regulatory compliance requirements.
Cybersecurity regulatory frameworks including industry-specific standards and national cybersecurity requirements increasingly apply to drone operations, particularly for organizations operating in critical infrastructure sectors or handling sensitive government information. Compliance with cybersecurity standards requires comprehensive documentation of security controls, regular security assessments, incident reporting procedures, and ongoing monitoring and improvement of security measures.
Privacy and data protection regulations create additional compliance obligations for drone operations that collect, process, or store personal information through surveillance activities, location tracking, or operational monitoring systems. Compliance with privacy regulations requires careful consideration of data collection practices, consent mechanisms, data retention policies, and cross-border data transfer requirements that may affect cloud-based fleet management systems and international operations.
Implementation Methodology and Continuous Validation
Professional drone security implementation requires systematic approaches that integrate security considerations into all aspects of drone operations from initial system design through operational deployment and eventual decommissioning. Security-by-design principles must be embedded throughout the development lifecycle, ensuring that security features are engineered into drone hardware, software, and operational procedures from the outset rather than being added as afterthoughts.
Threat modeling and risk assessment must be conducted early in drone system development and deployment phases, identifying potential vulnerabilities, attack vectors, and likely impact of various threats. This analysis informs security architecture decisions, control selection, and validation requirements that ensure security measures address the most significant risks while maintaining operational effectiveness and cost efficiency.
Regular security validation through penetration testing, red team exercises, and vulnerability assessments provides ongoing verification of security control effectiveness while identifying emerging vulnerabilities that require remediation. Validation programs should encompass technical testing of systems and networks, operational testing of procedures and personnel responses, and compliance auditing to ensure regulatory requirements are consistently met.
Continuous monitoring and improvement processes ensure that security measures remain effective as threat landscapes evolve and operational requirements change. Security metrics and key performance indicators should provide quantitative assessment of security program effectiveness while identifying trends and patterns that inform strategic security investments and operational improvements.
The comprehensive security of drone ecosystems represents both immediate operational necessity and strategic competitive advantage for organizations seeking to leverage unmanned aircraft capabilities while managing associated risks effectively. Success in drone security requires treating security as a fundamental design consideration rather than an operational afterthought, implementing comprehensive multi-layered defense strategies that address both cyber and physical threat vectors, and maintaining continuous validation and improvement processes that ensure security measures remain effective against evolving threats. Organizations that develop robust drone security capabilities will be positioned to leverage the full potential of unmanned aircraft technology while protecting operations, data, and stakeholders from the diverse and sophisticated threats that target modern drone ecosystems. As drone technology continues advancing and threat actors develop more sophisticated attack capabilities, comprehensive security expertise becomes an essential competency for successful drone operations across all application domains and operational environments.
 airdronehub.com
airdronehub.com